One of our Recent enterprise projects required designing a micro-service infrastructure with Windows authentication. We achieved this by implementing an OpenID infrastructure using IdentityServer3
What we are going to do?
- Setup and configuration of the IdentityServer3.
- Creating a client for the IdentityServer3 with Flows.Other and AllowedCustomGrantTypes: "windows".
- Setup and configuration of the WindowsAuthenticationService.
- Creating a custom grant validator in IdentityServer3 for windows grant type.
- Creating a console client and get a token from IdentityServer3 by using the current Windows principal.
How does this all communicate?
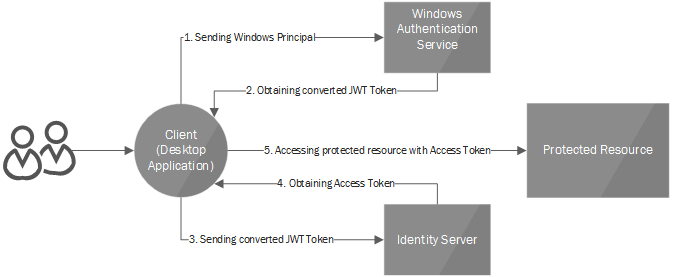
The client (in our case a WPF-based desktop application) calls WindowsAuthenticationService for converting his/her current windows principal to jwt token, which is trusted by IdentityServer3. On the next step, the Client calls the IdentityServer’s /token endpoint (using custom grant: windows ), including in the request the jwt token got from WindowsAuthenticationService. IdentityServer3will then issue a new token with requested scopes, custom claims and etc.
